Preventing Client-Side Access Token Abuse
Unfortunately there is no silver bullet here -- all analytics services have this problem too (Google Analytics, Mixpanel, etc.).
Our best practices for mitigating this problem:
Access tokens Use a separate client-side token with post_client_item scope only. (This is the default post_client_item token.) The client-side access token can only be used to send events and only from client-side platforms. It can't be used to read any data, and it can't be used to spoof server-side events.
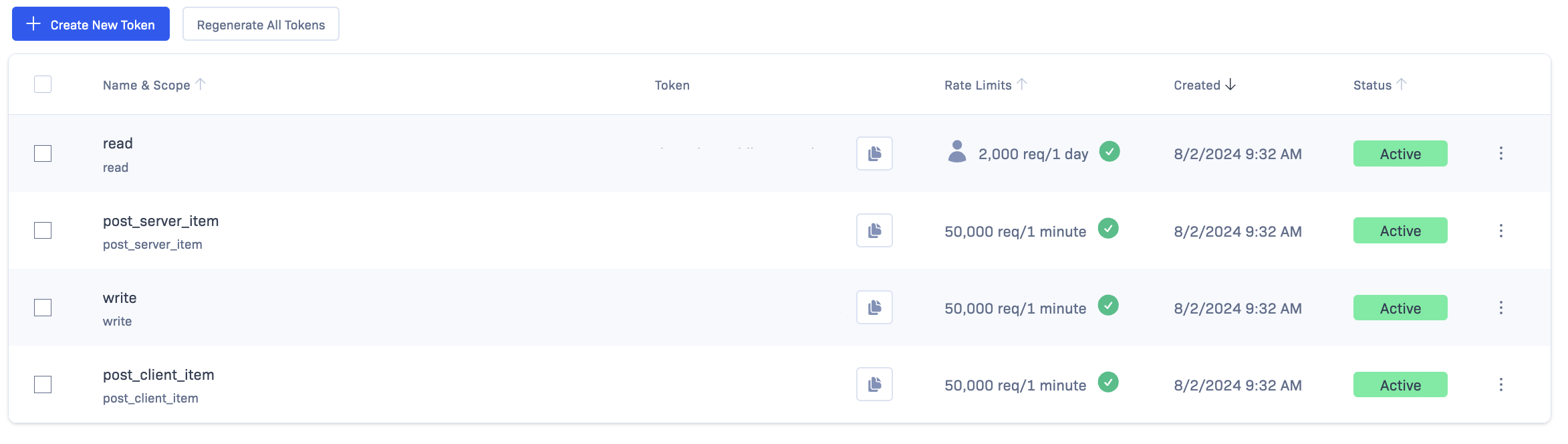
Tokens can be disabled and replaced at any time. If someone is abusing your token, you can disable it and use a new one instead.
IP Blocklist We also provide an IP Blocklist so that you can blocklist specific malicious IPs. You can find the source IPs in the Rollbar interface, and then add those IP(s) to the blocklist. (Project -> Settings -> IP Blocklist)
Updated over 1 year ago